Everybody’s worried about Internet security these days – and they darn well should be. Especially when we’re talking about services whose whole raison d’etre is sending secure messages. That’s why people’s alarm bells started ringing over the weekend when a big scandal blew up about WhatsApp and its security: somebody had supposedly discovered a backdoor to the app that allowed people to read user chats. Turns out, though, that there’s no need to freak out as that rumor is not quite correct.
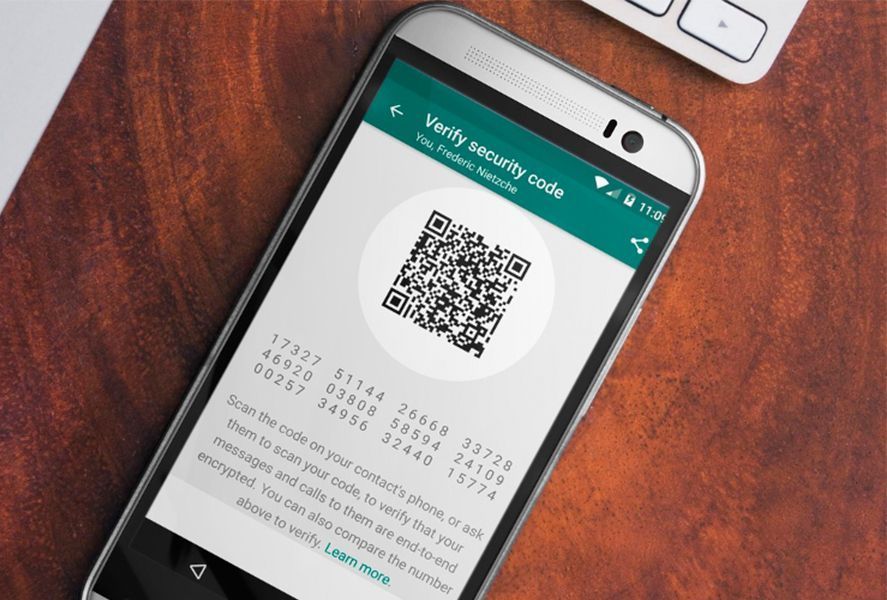
All the brouhaha of recent days stems from a Guardian article clamoring about the vulnerabilities of WhatsApp. According to the piece, this danger comes from a code snippet on WhatsApp that generates encrypted keys when you’re not connected and the second checkmark still has not appeared. That could be used by government agencies to spy on users, says Tobias Butler, an encryption expert who discovered this key generation.
While it’s true that there’s a way to generate encryption keys, it’s highly unlikely that they can be used to spy on your messages. To understand this a bit better, we have to talk a bit about the Signal protocol, which is the encryption system implemented by WhatsApp and deemed the best system out there for use with instant messaging. This protocol, developed by Open Whisper Systems in 2013, is already used for certain functionalities on other apps besides WhatsApp: on secret conversations on Facebook Messenger, for instance, and the incognito mode for Google Allo.
It's ridiculous that this is presented as a backdoor. If you don't verify keys, authenticity of keys is not guaranteed. Well known fact.
— Frederic Jacobs (@FredericJacobs) January 13, 2017
The Signal protocol is an “end to end” encryption system based on the generation of unique keys for each WhatsApp user. This security method has been defended by several experts on the subject, brought together here by Gizmondo. The confusion arose from one of the steps taken by this system: the security keys change when the app is reinstalled or you change phones. This means it’s possible that in a chat where one person has just installed the app, the new keys have not yet been sent. This creates a sort of vacuum in which the new keys are sent and verified between the two devices. But as Open Whisper Systems explains on its blog, this isn’t a vulnerability – it’s just a feature of the system.
There’s nothing to fear here, folks, as it’s been shown that no security problems exist. Still, if you’re worried anyway you can always pick an alternative IM app and try it out. Telegram is a good one, as we mentioned in our recent list of free open source apps.
WhatsApp for Android on Uptodown [APK] | Download










Boa noite