Activity monitoring software is currently one of the most active markets. There are literally dozens of applications designed to control activity from any device, whether it be from a mobile device or desktop computer. Genuine software of this type is focused on providing parental control for computers used by children, or on monitoring employees in their respective positions. However, in every case, these kinds of programs can also be used for illegal activity, such as stealing passwords and accessing private information.
There are both hardware and software keyloggers, which means that even though your antivirus doesn’t detect any type of control software, you could connect keylogger hardware to the USB port via the keyboard, or in its older version, the PS/2 port. These types of hardware used with malicious intent seem more like something that James Bond would use, such as a keylogger soldered to keyboard circuit, hidden underneath the casing. In the end, the objective of these systems is to record all the keystrokes made from the keyboard, or even take screen shots remotely, in addition to the consequences that doing so brings with it.
Its software version is what is commonly known as spyware, which, compared to keyloggers, has the great advantage that it can remotely access information. There are many free options to choose from, such as Keylogger Douglas, KidLogger, or Revealer Keylogger. Likewise, there is also software that keeps your activity from being recorded, keeping you safe from it being used inappropriately, such as SafeKeys.

All activity performed on your computer can be recorded, from the websites you visit, your file activity, conversations with clients on instant messaging, even to recording audio that you play on your computer, regardless of its origin.
Additionally, keyloggers are used legally to control children’s computer use at home, or to control employee computer use. You can monitor which websites are accessed, and even conversations that co-workers have via instant messaging services that use the company’s private network. Although this can be legal, it isn’t very ethical, as in many cases social networks and certain email providers are allowed to be used during break time, which means that the company would have access to the employee’s private accounts.
On the other side of the coin are all the ways you can abuse a keylogger, such as stealing passwords, spying, or the common theft of online banking usernames and passwords. Depending on the keylogger’s complexity, the information that is taken can be saved in a hidden file on the hard drive of the victim’s computer until someone accesses it as you normally would access a file or it can also be sent anonymously by email, and even through an FTP server to anywhere in the world once the victim connects to the Internet.
In light of these illegal practices, and so you don’t end up like Sandra Bullock in the movie “The Net”, it’s always recommended that you have an updated antivirus. Or, in the event that you need to connect to the Internet from a computer you don’t trust, you can use an antivirus to test the background activity of the USB or PS/2 port to see if there is any device illegally collecting information.



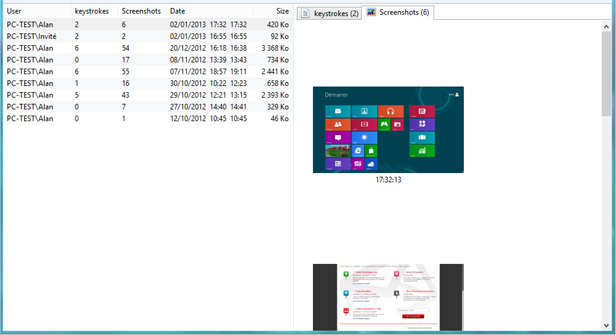



[…] you instructions on how to install a “protective” program, which is in fact nothing more than a keylogger or a malware to remotely control your […]